The Internet of Things (IoT) has transformed how devices interact, communicate, and function. It has led to significant advancements in various fields, including smart homes, healthcare, industrial automation, and more. However, this interconnected network has also introduced numerous security challenges.
According to a report by Forbes, the number of connected IoT devices is expected to reach 30.9 billion by 2025, highlighting the vast potential for vulnerabilities. Additionally, a study by Ponemon Institute found that 63% of organizations experienced a data breach due to an IoT device in the past year.
As IoT continues to expand, the urgency for robust security measures becomes even more critical. Gartner estimates that by 2025, more than 75% of the enterprise-generated data will be created and processed outside of centralized data centers or the cloud, increasing exposure to potential threats.
A report from Ampcus Cyber reveals that 90% of IoT devices have at least one critical vulnerability, with many lacking basic security protocols. With an alarming 37% increase in malware attacks on the IoT devices in the past year, the need for strong authentication mechanisms and proactive measures to secure IoT environments is more important than ever. The lack of substantial security in these devices not only jeopardizes personal and organizational data but can also lead to critical failures in essential operations.
To address these security challenges, the use of Entity Attestation Token (EAT), along with Intertrust technology, can enhance trust and standardize information on IoT devices, providing a robust mechanism to verify the integrity and identity of IoT endpoints in IoT ecosystems.
What are the most common threats to iot devices?
IoT devices are increasingly vulnerable to a variety of threats; here are the four most typical:
- Man-in-the-middle (MITM) attacks pose a significant threat during data transmission between Internet of Things (IoT) devices, because it enables attackers to intercept and manipulate the data being exchanged. This form of attack can lead to severe consequences, including data theft, unauthorized access, and the manipulation of commands, jeopardizing the integrity and confidentiality of the information shared.
- Denial of service (DoS) attacks illustrate another vulnerability within IoT systems, where an attacker inundates devices or networks with excessive traffic. Such overwhelming actions can render these devices nonfunctional, disrupt vital operations, and result in notable downtime.
- Firmware exploits represent a critical area of concern for IoT deployments. Many devices operate on firmware that may harbor vulnerabilities, enabling attackers to gain unauthorized control, install malicious software, or compromise the device’s functionality.
- Physical attacks further exacerbate the risks associated with IoT devices, particularly since they are often situated in remote or unsupervised locations. These vulnerabilities allow attackers to physically tamper with devices, manipulate their hardware, or extract sensitive information, underscoring the need for comprehensive security strategies to protect against various threats in the IoT ecosystem.
What is an Entity Attestation Token?
The Entity Attestation Token (EAT) is a security framework designed to enhance the trustworthiness of IoT devices by providing a standardized way to convey security-relevant information about an entity (such as a device) to another entity. Developed and defined by the Internet Engineering Task Force (IETF), EAT serves as a digital token that attests to various attributes and characteristics of a device.
At its core, EAT is structured to encapsulate a wide range of information, including device identity, hardware and software configurations, operational status, and security posture. This information is critical for establishing a chain of trust between devices, ensuring that they can be securely integrated into larger systems.
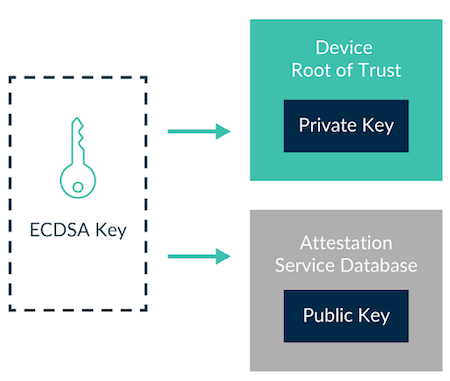
Attestation typically uses a signing algorithm like Elliptic Curve Digital Signature Algorithm (ECDSA). In this step, the private part of the ECDSA key is put into a secure location in the device hardware or chip, called the Root of Trust (RoT). This key will be used to sign the attestation token and the private part is kept secret so that the relying party knows the signature could only have come from an authentic device.
This is the fundamental basis for attestation security. Correspondingly, the public part of the ECDSA key goes into a database housed by the attestation service. This will be used to verify the signature on the attestation token
EATs can be implemented using different encoding formats, most notably JSON Web Tokens (JWT) and Concise Binary Object Representation (CBOR) Web Tokens (CWT). These formats allow EATs to be flexible and compatible with various communication protocols and environments.
Furthermore, EATs utilize digital signatures or Message Authentication Codes (MACs) to ensure the integrity and authenticity of the attested information, preventing tampering and unauthorized modifications.

There are several key features associated to EAT such as:
- Standardization. EAT is a standardized protocol, ensuring consistency and interoperability across different devices and platforms.
- Lightweight. EAT uses JSON Web Tokens (JWT) or Concise Binary Object Representation (CBOR) for encoding, making it suitable for resource-constrained IoT environments.
- Signed tokens. EATs are digitally signed, providing authenticity and integrity. The signature ensures that the token has not been tampered with and is from a trusted source.
- Attribute attestation. EAT can convey various attributes such as device identity, firmware version, hardware configuration, software state, and more.
- Scalability. Designed for large-scale IoT deployments, EAT can be efficiently implemented across numerous devices.
What are the threats that EAT can protect against?
EAT provides robust protection against several critical threats in IoT environments. Here are the key threats EAT can mitigate:
- Identity spoofing. EAT provides verifiable identity information about a device. This ensures that unauthorized devices cannot masquerade as legitimate ones, thereby preventing identity spoofing.
- Data tampering. Since EATs are digitally signed, any tampering with the token can be easily detected. This ensures the integrity of the attested information.
- Firmware and software attacks. EAT can attest to the firmware version and integrity, helping identify devices running outdated or compromised firmware. This enables timely updates and prevents exploitation of firmware vulnerabilities.
- Unauthorized configuration changes. EAT can include information about device configuration, allowing for the detection of unauthorized changes. This helps maintain the intended operational state of the device.
- Man-in-the-middle attacks. EAT helps establish secure communication channels by providing trusted device attributes. This reduces the risk of MITM attacks by ensuring that only trusted devices can communicate.
- Device impersonation. Malicious actors attempt to impersonate legitimate IoT devices to gain unauthorized access to networks and data. EAT provides strong device authentication, ensuring that only verified devices can communicate with other devices and services.
- Boot-time attacks. These are the attacks that exploit vulnerabilities during the boot process to load malicious firmware or software. EAT supports secure boot processes by providing attestation of the boot state, ensuring that the device boots with trusted software.
- Malware infections. EAT can provide continuous attestation, ensuring the device remains in a known good state and preventing the execution of malicious software.
- Supply chain attacks. Compromised components are introduced into the device during manufacturing or distribution. EAT provides a chain of trust from manufacturing to deployment, verifying each component’s integrity and authenticity.
- Configuration drift. Devices drift from their intended configurations, introducing security vulnerabilities. EAT can include configuration attestation, ensuring that devices operate with approved settings.
- Insider threats. EAT can help detect and prevent unauthorized changes or access attempts by providing detailed attestation of device states and actions.
- Replay attacks. Malicious actors capture and reuse legitimate messages to perform unauthorized actions. EAT can include nonce or timestamp information to ensure that each attestation is unique and timely, preventing replay attacks.
What Are the Benefits of EAT?
The implementation of EAT in IoT ecosystems offers numerous benefits, enhancing security, interoperability, and trustworthiness. Here are the primary advantages:
- Enhanced security. EAT provides a robust mechanism for conveying security-relevant information, significantly enhancing the overall security posture of IoT deployments.
- Interoperability. As a standardized framework, EAT ensures interoperability across different devices, manufacturers, and platforms. This is crucial for large-scale and heterogeneous IoT environments.
- Scalability. EAT’s lightweight nature makes it suitable for a wide range of devices, including those with limited computational resources. This ensures scalability across diverse IoT ecosystems.
- Trust establishment. EAT facilitates the establishment of trust between devices and other entities, which is essential for secure interactions and transactions in IoT environments. It helps establish a chain of trust from the device to the service provider, ensuring that each component in the communication path is trustworthy.
- Regulatory compliance. EAT can help meet various regulatory and compliance requirements by providing verifiable information about device attributes and security status. This is increasingly important as regulatory bodies impose stricter security standards on IoT devices.
- Simplified device management. EAT provides a standardized way to manage and verify device attributes, simplifying device management and maintenance tasks.
- Integrity. EAT allows for the verification of the integrity of a device’s hardware and software and protects against tampering, malware and unauthorized modifications to the device.
- Provision of evidence. EAT provides evidence of device security posture, including hardware and software configurations and their runtime state to help against misconfiguration, insecure states and deviations from known good configurations.
- Secure boot and firmware. EAT can be used to attest to the secure boot process and the integrity of the firmware to protect against firmware attacks, including boot-time malware and unauthorized firmware updates.
- Support for remote attestation. EATs support remote attestation, allowing remote verification of a device’s security state to prevent physical access attacks and unauthorized local changes to the device.
- Contextual information. EAT can include contextual information such as location, device type, and operational status, enhancing situational awareness.
How does XPN support EAT?
Explicit Private Network (XPN) is an Intertrust security feature designed to provide enhanced security for network communication by creating a secure, isolated environment for data exchange. XPN is particularly relevant for IoT ecosystems, where secure and reliable communication between devices is critical. Here’s how XPN supports Entity Attestation Token (EAT):
- Secure communication channels. XPN ensures that there is a secure communication channel established between XPN enabled entities such as devices, servers, and gateways. This secure channel ensures that the data, including EATs, is transmitted without interception or tampering. XPN protects the integrity and confidentiality of the attestation tokens during transmission.
- Authentication and trust. EATs are used to convey security-relevant information about an entity. XPN enhances the trustworthiness of these tokens by providing a secure environment for their exchange. The secure communication channel established by XPN ensures that the entities involved in the communication are authenticated, reducing the risk of man-in-the-middle attacks and ensuring that only trusted entities can exchange EATs.
- Access control. XPN can enforce strict access control policies, ensuring that only authorized devices and users can access the network and exchange EATs. By integrating access control with the attestation process, XPN ensures that devices that do not meet the required security standards (as indicated by their EATs) are denied access to the network.
- Integrity and authenticity. EATs use digital signatures or Message Authentication Codes (MACs) to ensure their integrity and authenticity. XPN complements this by providing secure transport, ensuring that the tokens are not altered during transmission. This double layer of protection—at both the token and transport levels—ensures that the attested information remains trustworthy.
- Compliance and monitoring. XPN can be integrated with monitoring and compliance systems to ensure that all entities within the network adhere to the required security policies. By using EATs, XPN can continuously assess the security posture of devices and take necessary actions if any device is found to be non-compliant. This dynamic assessment and enforcement enhance the overall security of the network.
Conclusion
The proliferation of IoT devices brings significant benefits but also introduces substantial security risks. The Entity Attestation Token (EAT) provides a robust framework for enhancing the trustworthiness of IoT devices by conveying verifiable security-relevant information. EAT protects against a range of threats, from identity spoofing to unauthorized configuration changes, and offers numerous benefits, including enhanced security, interoperability, and scalability.
The support of EAT by XPN further strengthens the security of IoT communications, ensuring that attested information is transmitted securely and remains intact. Together, XPN and EAT provide a secure, authenticated, and controlled environment for the exchange of attestation tokens, enhancing the overall security and trustworthiness of the networked devices.
About Apurva Sachan
Apurva Sachan is a product strategy consultant at Intertrust and MBA candidate (Class of ‘25) at the University of Virginia’s Darden School of business. Prior to this, Apurva spent 6 years at Deloitte Consulting, working majorly on data modernization for a US based energy client. She has a B.Tech degree in electronics engineering from VIT Vellore.